Ransomware is a persistent — and growing — threat. From the uptick in straightforward attacks to as-a-service variants that let would-be hackers purchase and deploy malware “starter kits,” the ubiquity and efficacy of ransomware attacks is a problem no company can ignore. Ransomware threats are now worrisome enough that businesses have taken a critical step: They’re taking security seriously and making cyber-defense efforts a line-of-business priority. The problem? Hackers aren’t taking the newfound fortitude of businesses lying down, redoubling their efforts to find malware solutions that can slip through network security undetected, wreak havoc and produce big payments.
How Ransomware Uses Powershell from CrowdStrike
Growing Threat
It’s not just corporate perception that pegs ransomware threats as more prevalent and dangerous. In Q1 2016 alone, new ransomware variants were up 17 percent, and the FBI predicted $1 billion in revenue for ransom-based hacks worldwide. Two factors drive this expansion: (1) increased attack surface, and (2) corporate worry about the results of a successful attack.
Consider the vast number of mobile devices now in use across corporate America, combined with the growing number of always-connected sensors, POS terminals and “smart” appliances that provide easy access to the periphery of supposedly secure business networks. Add the potential PR nightmare that comes with locked-out files containing personally identifiable information (PII) or financial data, and it’s no surprise that many companies are willing to pay rather than risk the aftermath of a successful attack — giving ransomware makers the encouragement they need to create increasingly complex code.
Big Impact
What’s the real impact of a successful ransomware attack? First is cost. Chances are attackers will ask for payment in Bitcoins — and right now the price of a single coin hovers around $1,000 U.S., meaning these attacks get very expense, very fast. There’s also the cost incurred to clean networks after a ransomware attack is over. Security professionals need to ensure corporate systems are safe and secure, and then implement new defensive measures to ensure the same type of attack isn’t successful again.
Data loss is another critical impact: If companies refuse to pay and hackers carry out their threat to destroy data, this could seriously harm both day-to-day operations and long-term goals. Ideally, firms should back up all critical data redundantly and off-site, but if no backups exist or aren’t immediately available, companies can also suffer from prolonged downtime. Every hour that systems aren’t up and running, employees can’t access critical programs and customers can’t contact your business results in mounting losses, meaning the initial impact of a malware infection often pales in comparison to long-term effects.
New Iterations
While companies are getting wise to many basic ransomware tactics — for example, one as-a-service variant relies on open-source code from the Hidden Tear project, which has been cracked by multiple security teams — hackers are developing new methods of infection and execution, able to bypass current detection methods and compromise corporate networks.
Also Read
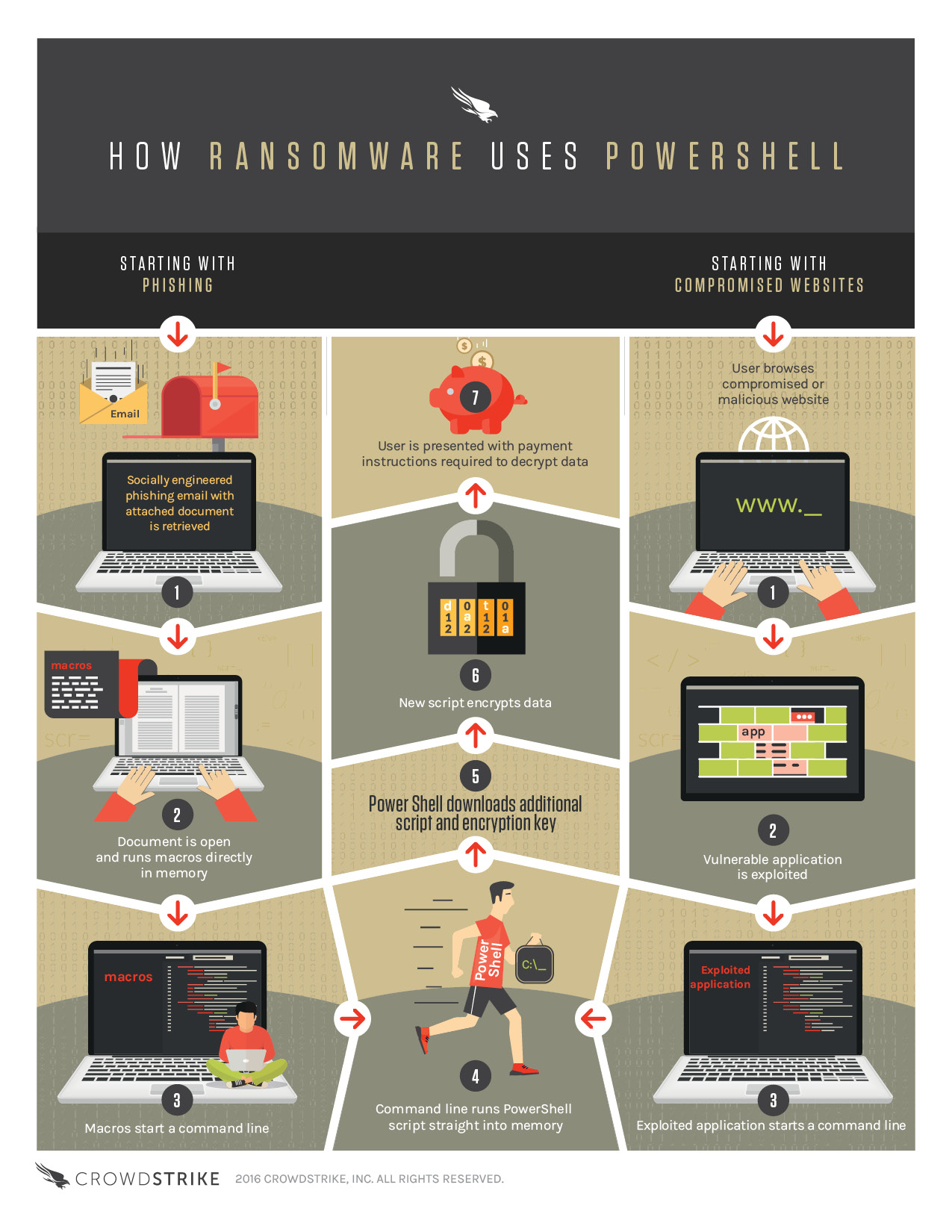
One evolving attack vector is “fileless” ransomware, which opts out of the file attachments typically associated with ransom efforts, and instead leverages PowerShell to bypass security controls and download malicious code. Two methods produce the same end result: In the first, users are directed to a compromised or malicious website that exploits a vulnerable application. This app starts a command line, and then runs PowerShell to download additional scripts and encryption keys. In the second method, users receive a socially engineered phishing email with a document attachment. The document contains macros with malicious code, which in turn start a command line and run PowerShell. In both cases, the naturally trusted status of PowerShell and the absence of any “typical” ransomware files help attackers bypass security systems.
Concerned about ransomware? See the accompanying infographic to learn more about fileless techniques to evolve your defensive posture, then leverage advanced machine learning and attack detection solutions to help safeguard your critical data.
